I ran in to
this super clear explanation from Damian Scoles on how to configure remote PowerShell over SSL when my remote PowerShell wasn't working.
I covered the same subject once before here -
remote-powershell-sessions-for-ad
This goes on step further in securing the session:
For Office365 an SSL connection to remote PowerShell is default.
$LiveCred = Get-Credential
$Session = New-PSSession -name ExchangeOnline -ConfigurationName Microsoft.Exchange -ConnectionUri https://ps.outlook.com/powershell/ -Credential $LiveCred -Authentication Basic -AllowRedirection
Import-PSSession $Session
Also note that the authentication type is BASIC.
If you try to force the PowerShell virtual directory to only accept SSL, you break local PowerShell access:
Set-PowerShellVirtualDirectory -Server ex01 -RequireSSL $true

Now that PowerShell access is broken we cannot run PowerShell commands to fix the PowerShell Virtual Directory? So switch to IIS Manager. At the PowerShell virtual directory ‘Require SSL’ is checked:
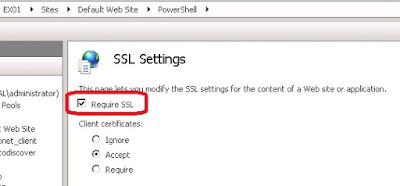
Uncheck the box and click apply.

Local Exchange PowerShell is working again.
Now how do we enable SSL remote PowerShell?
Lets make sure we can do PowerShell remoting over HTTP:
Verify it’s enabled:
Enter-PSSession -ComputerName localhost
If you receive an error, then PowerShell remoting can be enabled with this command:
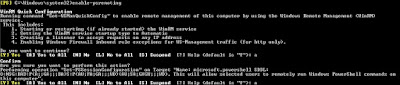
Enable-PSRemoting
Choose ‘A’ for the answer to the two questions:
Now that we have PowerShell enabled, verify the user account you want to connect with has access:
Get-User <alias> |ft displayname,*power*,
If the result is True, then the user has permission to connect remotely via PowerShell.
What about SSL? Let’s see what happens by default:
New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri http://<exchange server FQDN>/PowerShell/ -Credential (Get-credential) -Authentication Kerberos
** Note ** Using Basic for Authentication method will cause the connection to fail. Either have no
Authentication defined, or choose something like kerberos in our example.
You will be prompted for credentials and allowed to connect. If however the connectionURI contains HTTPS and not HTTP, it will fail.
New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://<exchange server FQDN>/PowerShell/ -Credential (Get-credential) -Authentication Kerberos
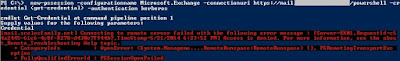
So what is the fix? IIS Authentication. The PowerShell virtual directory has no authentication settings configured
Get-PowerShellVirtualDirectory -Server <Exchange Server> | fl *auth*
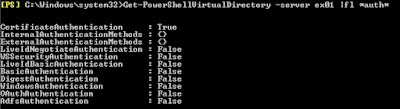
Notice that no authentication is configured by default. Let’s enable Basic Authentication as this will allow us to use an SSL connection to remotely connect via Powershell.
Get-PowerShellVirtualDirectory -Server <exchange server> | Set-PowerShellVirtualDirectory -BasicAuthentication $true
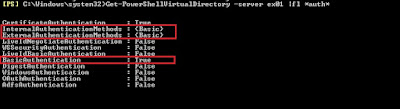
Now that we have verified PowerShell Remoting is enabled, that our user account has access and that Basic Authentication is enabled, we should be able to connect via HTTPS:
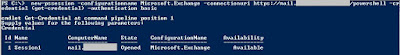
We now have a successful connection to our remote Exchange 2013 server over HTTPS.
Source























